NQ Contacts Backup & Restore is an android app that allows users to backup and restore contact data (as vcard) to/from the remote NQ server. For the audit, the android app was the primary target.
Note: The app shares its code base with NQ Mobile Security & Anti Virus - hence the odd class names for a simple contact backup app.
CVE-2017-15999: Lack of HTTPS usage
When logging in or transmitting data, the app communicates with the remote server via HTTP. This can be exploited in various ways. One of these is sniffing the request when a user logs in:
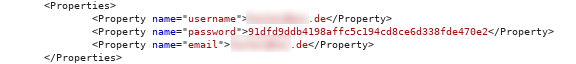
As you can see, the username is being transmitted in cleartext. The password is hashed with SHA-1. An attacker can now crack the SHA-1 hash (because that’s pretty easy nowadays):

Additionally, an attacker could use the sniffed hash to download the stored contacts from the server directly. As described later, the attacker can also access transmitted contact data.
Summary
The CVE details can be found here
| Vulnerability Type | Plaintext data transport |
| Affected Product Code Base | NQ Contacts Backup & Restore - 1.1 |
| Affected Component | Basically every component executing network action. For the login process: ContactAccountLogin and ContactAccountSwitch |
| Impact | Information Disclosure of sensitive data (login data) |
CVE-2017-15997: RC4 encryption with a static key
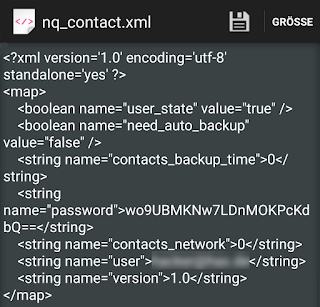
The app uses the RC4 stream cipher to encrypt/decrypt password stored in the android shared preferences. The file looks like this:
The decryption routine, which can be found in DataUtils, look as follows:
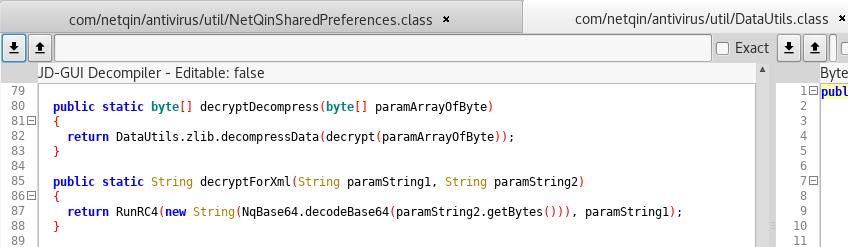
The stored value is base64-decoded and passed to the RC4 algorithm. The first parameter of decryptForXml is a static key, as you can see here:
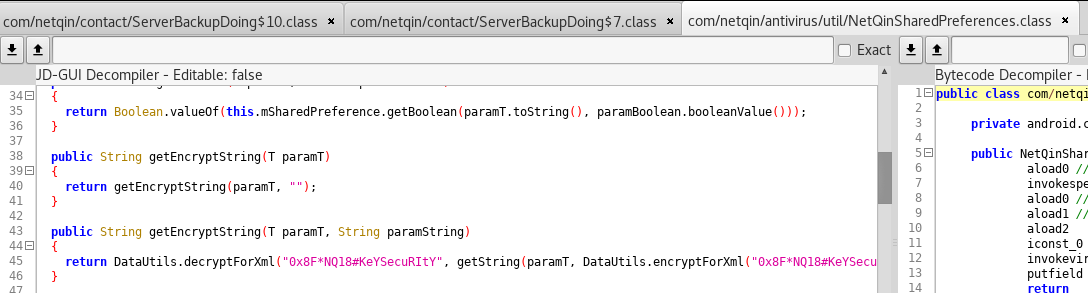
Using this knowledge, it’s easy to decrypt the stored password value from the shared preferences XML file:
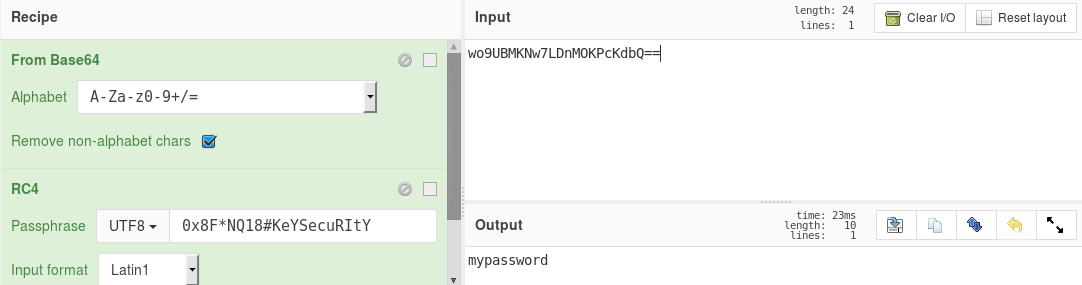
This makes it easier for an attacker to decrypt login data of users.
Summary
The CVE details can be found here
| Vulnerability Type | Usage of a static encryption key |
| Affected Product Code Base | NQ Contacts Backup & Restore - 1.1 |
| Affected Component | NetQinSharedPreferences |
| Impact | Information Disclosure of login data |
CVE-2017-15998: DES encryption with a static key
When syncing user data (e.g. contacts as vcards), the app uses DES encrypted zip files, as you can see in the class ServerBackupDoing$7 :
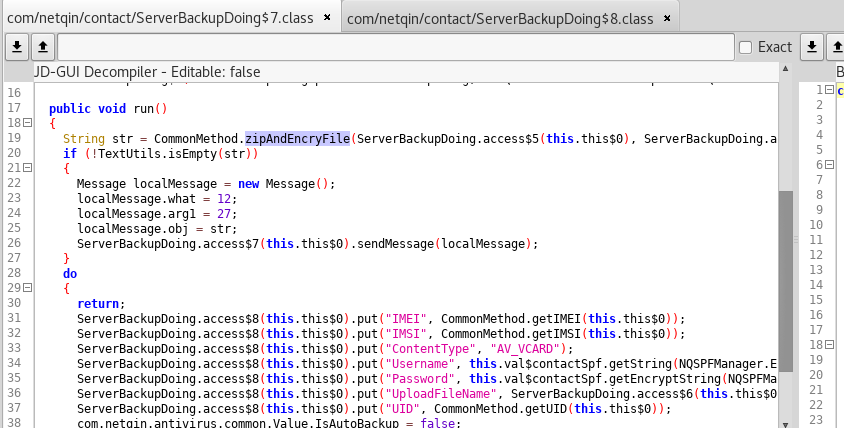
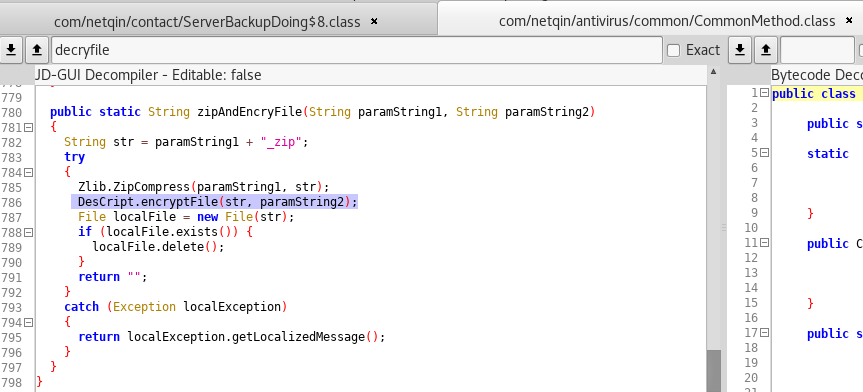
In the class DesCript, there exist two static keys:
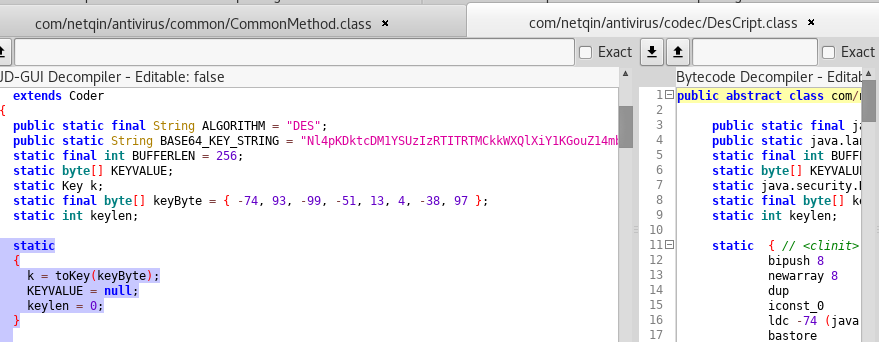
The key named keyByte is used to create a KeySpec, which represents the key being used to encrypt/decrypt data.
Because there is no HTTPS in place, it’s therefore possible for an attacker to gain access to sensitive contact data.
Summary
The CVE details can be found here
| Vulnerability Type | Usage of a static encryption key |
| Affected Product Code Base | NQ Contacts Backup & Restore - 1.1 |
| Affected Component | ServerBackupDoing, DesCript |
| Impact | Information Disclosure of contact data |