WriteDiary consists of a webapp and an Android app (version 4.72). For the audit, the android app was the primary target.
The developer and owner of both the webapp and android app has been contacted multiple times to develop a quick fix for the issues addressed in this blog post and a vulnerability concerning the webapp which isn’t described here. However, no response has been received. This is bad, as you will see in the first finding:
Embedded Management Credentails
Yes, really. The developer decided to embed his personal GMail credential in the Android app. These credentials may or may not work in the management interface of this product - of course I haven’t tried ;)
CVE-2017-15581: Lack of HTTPS-usage, lack of user data encryption when transmitting
In the “Diary with lock” (aka WriteDiary) application 4.72 for Android, neither HTTPS nor other encryption is used for transmitting data, despite the website states that the product is intended for “a personal journal of secrets and feelings,” which allows remote attackers to obtain sensitive information by sniffing the network during LoginActivity or NoteActivity execution. You can simply check the file strings.xml for api_url_prod with the value of http://diary.adpog.com/api2.
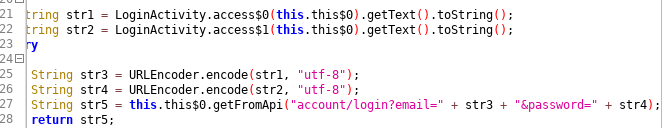
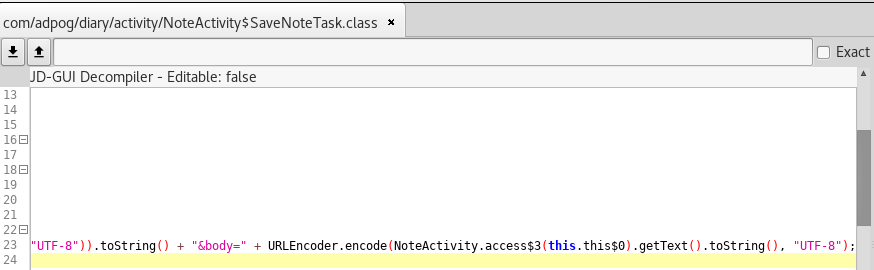
Summary
The CVE details can be found here
| Vulnerability Type | Plaintext data transport |
| Affected Product Code Base | WriteDiary - 4.72 |
| Affected Component | LoginActivity, NoteActivity |
| Impact | Information disclosure of sensitive user data |
CVE-2017-15582: Usage of static AES parameters
In net.MCrypt in the “Diary with lock” (aka WriteDiary) application 4.72 for Android, hardcoded SecretKey and iv variables are used for the AES parameters, which makes it easier for attackers to obtain the cleartext of stored diary entries:
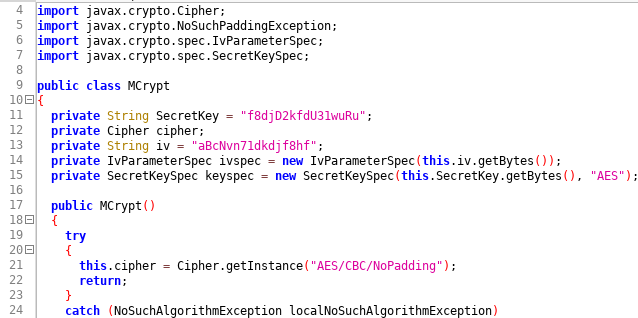
As you can see, the specific values are:
secret key = "f8djD2kfdU31wuRu"
iv = "aBcNvn71dkdjf8hf"
Summary
The CVE details can be found here
| Vulnerability Type | Hard coded AES parameters |
| Affected Product Code Base | WriteDiary - 4.72 |
| Affected Component | net.MCrypt |
| Impact | Information disclosure of sensitive user data |
Additional note
Further analysis showed that the data stored on the web application server is not encrypted. This means, that the whole concept isn’t as private as it claims it is. On top of that, there’s a built-in backdoor which lets the administrator access the confidential diary entries of every user.